US Intelligence Coup: Washington Post
Swiss Encryption company Crypto AG began working for the US government during World War II. Customers included 120 countries, including US allies that had no clue the company was “secretly owned by the CIA in a highly classified partnership with West German intelligence,” reports Greg Miller for the Washington Post. The purchase was made in 1970 through shell companies. The intelligence agencies adjusted the products to read encrypted messages, a mission decribed as among “the most closely guarded secrets of the Cold War” and “the intelligence coup of the century.” The agencies controlled the firm’s hiring, technology and algorithm design, and sales operations. The German spy agency BND abandoned the project in the early 1990s, and the CIA sold the company in 2018 to an unwitting buyer as more encryption products became available. The Soviet Union and China did not purchase the encryption programs, but the agencies could glean details from exchanges with other countries. Miller concludes that the program helped feed US desire for surveillance capabilities as well as official worries about products from other countries, whether Kapersky or Huawei. – YaleGlobal
US Intelligence Coup: Washington Post
No wonder the US worries about China’s Huawei: CIA and BND bought encryption-products firm and then read communications of allies and adversaries for decades
Wednesday, February 12, 2020
Read the article from the Washington Post about the control of an ecryption firm by the US CIA and the German BND.
Greg Miller is a national security correspondent for The Washington Post and a two-time winner of the Pulitzer Prize. He is the author of The Apprentice, a book on Russia’s interference in the 2016 US presidential race and the fallout under the Trump administration.
Reporting for this story was done in collaboration with Peter F. Mueller, a journalist and documentary filmmaker based in Cologne, Germany. Julie Tate in Washington contributed to this report.
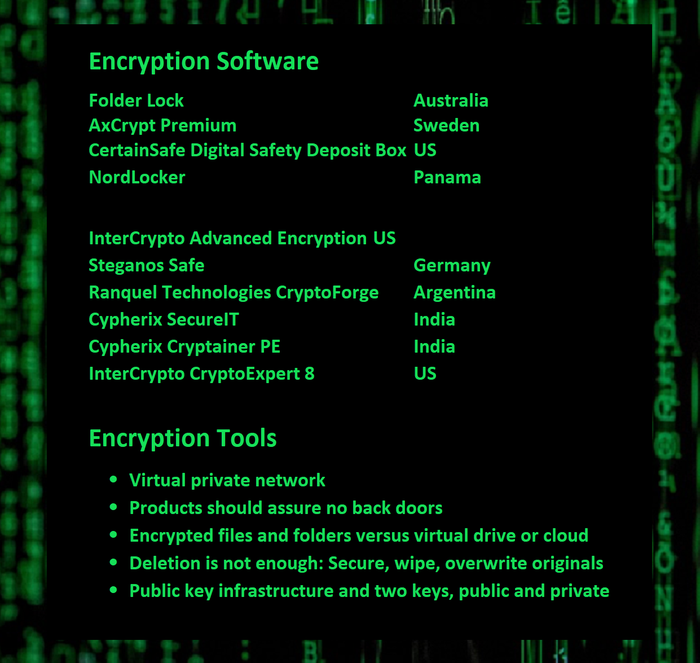
(Source: Data, PC Magazine and Wired; photo, Pxhere)
The Washington Post
washingtonpost.com © 1996-2020 The Washington Post